DAILY HACKING TIPS |
- How To Send Fake Emails
- How To Secure Facebook Account From Hackers
- Google Lauches A New Authenticating Process
- Website Hacking Best Techniques By Dailyhackingtips
- How To Hack Yahoo Accounts Easily
- How to update your Facebook status via Calculator
- Check SQL Injection in Best 3 Steps
- Free Reliance GPRS settings for reliance Mobiles
| Posted: 25 Nov 2011 11:20 PM PST After my post on How To Secure Facebook Account From Hackers , Today I am going to show you how to send fake emails. Ya fake emails, I know many of you ask this can we send Emails with others name, or other email address, ya you are right you can do this here. For those who didn't know what is fake mail for them I am discussing some terms related to them below. What is Fake Mail? A fake mail is mail in simple word a anonymous email. A fake mail is a mail in which the sender can send this mail to anyone without mention his/her original ID. Yes the site is Embei's Fake Mailer This site looks like this. Here you can give any Name, Email ID, Subject, Text. Name- This is the option from which the mail is to be send. Email-ID- Here you can give any Email-ID as per your choice. To- This is important as here you have to give the recipient's Email address. Subject- Anything as per your choice. Text- Anything as want to write and send it to the victim. And many other option as your per your requirement. Note: This post was only for Educational purpose. So remember don't use it for any illegal purpose or you only will be responsible. I Hope you really enjoy it !! |
| How To Secure Facebook Account From Hackers Posted: 25 Nov 2011 11:01 PM PST Facebook is always at the top of Hacker's list due to its large popularity, ease to use, connects large number of people, large collection of applications, many more. Facebook was launched in 2004, as of January 2011, it had more than 600 million active user. A hacker can get many useful information about anyone with Hacking his or her Facebook Account and can destroy anyones social life with it. Due to large number of attacks on Facebook everyday, it is trying to deeply secure its data from attackers. Many new awesome security feature had been built to secure its users, but loophole is always there. Some days before Facebook had built a new security feature, it is Login Approval similar to 2-Step Verification. As I have already mentioned a post about 2-step verification, if you have read that post then you must have some knowledge about it. Anyways back to the post. What is Login Approval? Login Approvals is an opt-in security feature similar to Login Notifications, but with an extra security step. With Login Approvals, each time you try to access your Facebook account from an unrecognized device (ex: any computer or mobile phone you haven't named and saved to your Facebook account), you will first have to enter a security code that's been sent to your mobile phone. How to turn on Login Approval? To turn on Login Approval in Facebook
What will happen after turning on the Login Approval? After turning on this feature whenever you will login to your Facebook Account from any other unrecognized devices you will be ask to enter a security code which will be sent to your mobile. You will see something like this: Google 2-Step Verification V/S Facebook Login Approval? Google 2-Step verification is far most better than Facebook Login Approval because Google 2-Step verification also provide some backup codes in case of mobile loss or other and in case when you can't receive verification code due to some network problem or else, you can also get a call from Google informing you about the verification codes, as compared to Facebook Login Approval. Facebook may also work hard to compete with Google 2-Step Verification. i hope you really enjoy it this post !! |
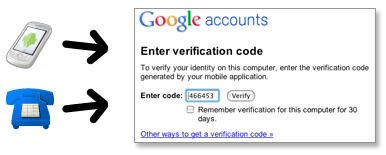
| Google Lauches A New Authenticating Process Posted: 25 Nov 2011 10:53 PM PST  Hello Today I am talking about a new authenticating process which Google had launced, its 2-step verification. Hello Today I am talking about a new authenticating process which Google had launced, its 2-step verification. Why you should use 2-step verification 2-step verification adds an extra layer of security to your Google Account by requiring you to have access to your phone – as well as your username and password – when you sign in. This means that if someone steals or guesses your password, the potential hijacker still can't sign in to your account because they don't have your phone. How you sign in with 2-step verification
What you'll needWhile 2-step verification requires some web savvy, you only need a few basic items:
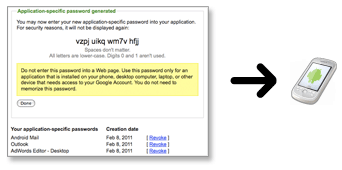
How to get startedGo to your Accounts settings page and look for the Using 2-step verification link. If you have the link, click it and start the setup process.If you do not see the link and you are a Google Apps user, you might have to access the 2-step verification setup through a special URL. It is also possible that your domain administrator has not yet set it up for your organization. Check with your domain administrator to find out. 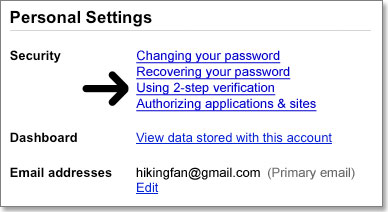 i hope you really enjoy it this post. If you have any queries ask me below. |
| Website Hacking Best Techniques By Dailyhackingtips Posted: 25 Nov 2011 10:39 PM PST Everyday, you search in Google, Yahoo, and other search engines, "How to Hack Websites?", "Methods to Hack Website", "Website Hacking", etc. Website Hacking have become a popular business or rather an interesting game for many people, reasons behind this hack is normally to prove their skills and to get fame, or anything else. As we know, "To catch a thief, we must think like a thief", like here also, we can conclude that to secure a things, we must first find insecure in it, then we can proceed on securing. So, before proceeding to the topic of securing we must first know what is insecure in it. There are many drawbacks by which websites are compromised, these is normally due to the poor management of site by the webmaster or admin. So, the methods by which websites are hacked are:
These are some of the common methods to hack a website, let's discuss them below.
Some others methods are DNS Hijacking, Insufficient Administration, Misconfiguration, Uses of Trojans, many more. My advice to all the webmaster or admin is to check their site against these vulnerabilities as to protect them from future attacks. I hope u really enjoy it !! |
| How To Hack Yahoo Accounts Easily Posted: 25 Nov 2011 10:30 PM PST This is my post at Dailyhackingtips Readers, I am very glad and happy to write it. I have heard a lots of people nowadays ask on How to Hack Gmail, Yahoo, Facebook, Youtube, Orkut, etc, etc. For them I am posting this hack. I hope you will really enjoy it and make use of it but don't use it for any harmful purpose and misuse it. So for this hack you will need a small program of which I will discuss below and tell you about on how to use it. The name of this wonderful program is Magic PS. Its a wonderful software utility which sends User ID and password of the victim to your yahoo account. Steps for Hacking:
Screenshot of the program: I will recommend you to use these option as shown in screenshot below: I hope you really enjoy it. |
| How to update your Facebook status via Calculator Posted: 25 Nov 2011 10:20 PM PST Another worthy post for Dailyhackingtips readers, in this I will show you "How to update your Facebook status via Calculator / NASA Satellite / Trojan Horse / etc / etc". With a rapid growing popularity among people about Facebook. it is really an awesome trick to fool your friends. You must have seen many status updates via fishy devices like calculator, iron, NASA Satellite, many more, now you would be thinking that "How is it possible?", in reality it is of-course not possible but still you can update your status by playing a trick. The trick is very simple, cool, and very effective. There are two ways which I have found by which you can update your status with these comical devices, one is very easy, you can do so using a website which allow you to do so, another is by using Facebook API keys (API key is an unique code that is assigned to the Facebook Apps when they are created). So, lets move on discussing them in detail. Step- 1 There is a website which allow Facebook users to update their status via amusing devices. The site contains a huge collection of cool gadget for updating the status. This method is pretty splendid.
Hurray! You have updated your text. Thats all, visit your profile and see the magic. Step- 2 This method involves the using of Facebook API keys, it much same like the above method. This method is much more interesting as in this we will be doing the update by ourself.
https://www.facebook.com/connect/prompt_feed.php?preview=true&api_key=API _Key
List Of Some Facebook API Keys Skynet (249284985083592) iPhone (6628568379) Blackberry (2254487659) Palm (7081486362) Sidekick (21810043296) Sony Ericsson (38125372145) Xbox LIVE (5747726667) iPad (112930718741625) Foursquare (86734274142) Telegram (140881489259157) Carrier Pigeon (130263630347328) Morse Code (134929696530963) Message in a Bottle (123903037653697) Commodore 64 (138114659547999) Your moms computer (132386310127809) TRS-80 (134998549862981) K.I.T.T. (129904140378622) Mind Computer Interface (121111184600360) eyePhone (110455835670222) toaster (203192803063920) microwave (0a5266c8844a1b09211e7eb38242ac2f) Super Nintendo Entertainment System (235703126457431) Gameboy Color (180700501993189) GoD (256591344357588) Glade Air Freshner (4aeb4db2e8df1cdb7f952b2269afb560) Strawberry (a4c9fb1708a848c2241674531176209b) The moon (221826277855257) Dr. Pepper (eea90d40e1d12565695dbbbdbd5e965b) Nintendo wii (243870508973644) Alcohol (250335888312118) Cheese (218791271497130) iPod Nano (142039005875499) Nintendo 64 (236264753062118) Microsoft Excel (242740155751069) Linux Ubuntu (220593361311050) iPhone 5g (211333348912523) My Bedroom (174811032586879) Your Mums Bedroom (5f64bbc9ac2f12b983200925da461322) Lamp (230755826955133) Your moms anus (b625297b655f0b46c86b68f754b82121) Refrigerator (250828364944350) A potato (127926427295267) Nasa Satellite (31d608d30292175bf7703149699ccb39) Vibrator (eb4c6d1a60e19a7795da501e1f468035) Sperm Whale (170318539700306) Pogo Stick (185103391549701) Banana Phone (1477a4cd29ec724a3de19be5d26e0389) Google+ (4d8243dbb7064f88351fe6c809582320) The Future (108372819220732) Smoke Signal (134138923334682) tin cans connected by string (242191299125647) Pokedex (de3da265cf6976745bb1d60a8c198151) Telepathy (ea01a57edb26cf1de143f09d45cfa913) Typewriter (d3d554bf60297cb2c384e3d7cf5a066d) Harry Potter (b8ebeb983f45eaa0bd5f4f66cad97654) TARDIS (200439256674396) Pip Boy (142806259133078) Mind Control (1dc633368924b3b0b4d08e3f83230760) Jedi Mind Control (240597869302110) Telekinesis (224139600960217) Post-It Note (115227201900831) GLaDOS (246126362083515) Ansible (185474028180003) W.O.P.R (228373497202865) Airwolf (123944137696757) HMCS Belafonte (222345601140304) Hogwarts (2dc1d3004dbc4a67c4b552be3c25ccb0) For instance, If you want to update your status using 'The Moon' just copy the API key, and paste it in the API key field like this: https://www.facebook.com/connect/prompt_feed.php?preview=true&api_key=221826277855257 I hope you really enjoy this post and will surely use it and also will fool your friends. But remember all these tricks can be done only when you are 'Logged In' in your Facebook Account. Please comment below to let me know if this really was informative and you all like it too. |
| Check SQL Injection in Best 3 Steps Posted: 25 Nov 2011 03:09 AM PST This is my post at Dailyhackingtips friends, I am very glad and happy to write it. I have heard a lots of people nowadays ask on How to Check SQL Injection I hope you will really enjoy it So Today I'm learning SQL injection (SQLi) indepth so I will try teaching you guys a little of that as well.SQLi is the most popular attack on any website these days.There has been an enormous increase in SQL programmers and websites,and the biggest problem with SQL is "Either your perfect/hacked".Due to poor coding programmers often leave vulnerabilities in their site and hackers its our job to inform them and patch them up.So lets see how to check if a site if vulnerable to SQLi Since this is still the basic,there is nothing much to do.All you have to is: 1.Get a site which uses SQL queries.For your convinc,in simpler terms it is any site which has "www.site.com/something.php?ex=43".You must have seen tons of such sites.Note: NOT all sites which have "=" use SQL queroes it might also use "PHP Get/Post method". 2.Once,you have a site like then just intersert a inverted comma(') like this "www.site.com/something.php?ex=43'". 3.If the site is vulnerable to SQL then it would return an error something like this.You might get an error like this "You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '\' AND single_group = "S"' at line 1" This error need not be the same always,as long as you get an error you can tell that the site is vulnerable to SQLi and its up to you to become a her and report to the site admin. Best Of luck Comment us For Batter Results |
| Free Reliance GPRS settings for reliance Mobiles Posted: 25 Nov 2011 02:27 AM PST This time we have come up with a free reliance smart gprs settings on the reliance mobile phones . We are getting large number of request and queries from the readers, requesting Free manual GPRS settings for Reliance Smart GPRS Settings: Here is the gprs settings for reliance for WAP, SMARTNET, MMS For SMARTWAP:Account name : SMARTWAP Access point name: SMARTWAP Home page: http://wap.rworld.co.in/gsm/index.wml Wapgateway proxy IP address: 97.253.29.199 Port: 8080 For SMARTNET:Account name: SMARTNET Access point name: SMARTNET Home page: http://www.google.co.in Wapgateway proxy IP address: 97.253.29.199 Port: 8080 For MMS:Account name: RTLMMS Access point name:MMS Homepage: http://10.114.0.5/mms/ Wapgateway IP: 10.114.0.13 Port: 9401 We hope the above provided settings will work to make your gprsactive. If the above settings does not help let us know throughcomments. |
| You are subscribed to email updates from Dailyhackingtips To stop receiving these emails, you may unsubscribe now. | Email delivery powered by Google |
| Google Inc., 20 West Kinzie, Chicago IL USA 60610 | |















No comments:
Post a Comment